Federation
Secure SSO
ADFS
SAML2 IdP
O365 SAML2 IdP
OIDC IdP
LDAP IdP
If you are federating your on-premise Active Directory (AD), SurePassID has the multi-factor authentication (MFA) you need.
 Secure SSO
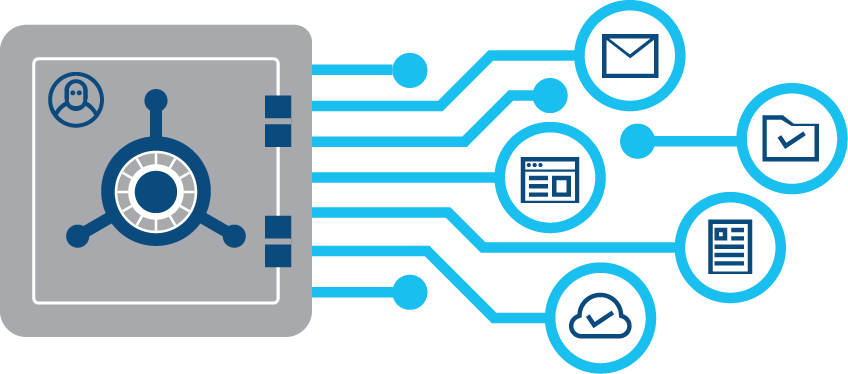
Secure SSO
SurePassID offers safe, one-click access to any application on-prem, in the cloud, or in hybrid environments. The result is outstanding user convenience and the elimination of inefficiencies associated with multiple logins and passwords across applications. Phishing-resistant MFA via FIDO2/WebAuthn passkeys takes Secure SSO to the "gold standard" of MFA, making it all but impossible for hostile state actors and ransomware gangs to compromise your users' single sign-on convenience.
Secure SSO is the combination of Single Sign-On (SSO) with multi-factor authentication (MFA). Secure SSO makes it easy to securely control the proliferation of URLs, usernames and passwords that come with cloud adoption. With one click users can authenticate with multi-factor authentication (MFA) and access their authorized applications, no matter what kind of cloud-connected device they are using. This increases user productivity and cost-effectiveness, while delivering the most secure and compliant solution available.
Deployment Options


Cloud
On-Prem


Hybrid Cloud
Air-Gapped
MFA Support


Phishing-Resistant MFA


Traditional MFA
 ADFS
ADFS
SurePassID seamlessly integrates with Microsoft Active Directory Federation Services (ADFS) 2.x, 3.0 and 4.0 to enable multi-factor authentication (MFA) for any services using federated logins. The result is a complete Zero Trust and regulatory compliance solution that locks down access to applications, networks, and data in IT/OT environments.
SurePassID supports any relying party that uses Microsoft’s WS-Federation protocol, like Outlook Web Access, SharePoint and Office 365. We also support SAML 2.0 federated logins for cloud applications like Google Apps, Box and Salesforce. The SurePassID ADFS 2FA adapter supports ADFS 2.x on Windows Server 2008 R2, and ADFS 3.0 and 4.0 on Windows Server 2012 R2, 2016, 2019 and 2022.
Deployment Options


Cloud
On-Prem


Hybrid Cloud
Air-Gapped
MFA Support


Phishing-Resistant MFA


Traditional MFA
 SAML2 IdP
SAML2 IdP
SurePassID adds a seamless layer of phishing-resistant security to application logins using the Security Assertion Markup Language (SAML) 2.0 authentication standard. SurePassID acts as an identity provider (IdP), authenticating users with their existing directory credentials and prompting for multi-factor authentication (MFA) before permitting access to the application.
SurePassID comes with a library of pre-configured Software-as-a-Service (SaaS) applications such as Salesforce, Zoom, and more. You can also add any SAML-enabled app with our generic SAML Service Provider tool.
Most importantly, SurePassID SAML 2.0 IdP deploys on-prem or in the cloud, ensuring MFA is available across IT/OT environments.
Deployment Options


Cloud
On-Prem


Hybrid Cloud
Air-Gapped
MFA Support


Phishing-Resistant MFA


Traditional MFA
 O365 SAML2 IdP
O365 SAML2 IdP
Since Microsoft does not release or document its Office 365 API for third parties, SurePassID has created our own O365 SAML2 IdP to add multi-factor authentication to O365 user logins. We accomplish this via the Security Assertion Markup Language (SAML) 2.0 authentication standard and custom integration code.
The result is seamless second factor support and phishing-resistant multi-factor authentication for the Microsoft O365 platform. The same SurePassID user experience is maintained for users, who can use their existing passkeys or tokens to access all federated applications. Thus we deliver a complete Zero Trust and regulatory compliance solution that locks down access to applications, networks, and data in IT/OT environments.
Deployment Options


Cloud
On-Prem


Hybrid Cloud
MFA Support


Phishing-Resistant MFA


Traditional MFA
 OIDC IdP
OIDC IdP
OpenID Connect (OIDC) is an interoperable authentication protocol based on the OAuth 2.0 family of specifications. It uses straightforward REST/JSON message flows with a design goal of “making simple things simple and complicated things possible”. It’s uniquely easy for developers to integrate compared to preceding identity protocols.
OpenID Connect lets developers authenticate their users across websites and apps without having to own and manage password files. For the app builder, it provides a secure, verifiable answer to the question: “What is the identity of the person currently using the browser or native app that is connected to me?”
SurePassID acts as an OIDC identity provider (IdP), authenticating users with their existing directory credentials and prompting for multi-factor authentication (MFA) - either one-time password (OTP) or phishing-resistant (FIDO2) - before permitting access to the application.
Deployment Options


Cloud
On-Prem


Hybrid Cloud
Air-Gapped
MFA Support


Phishing-Resistant MFA


Traditional MFA
 LDAP IdP
LDAP IdP
Lightweight Directory Access Protocol (LDAP) is a legacy protocol used for accessing directory services and directory resources (“entries”). It’s typically used by companies to facilitate access to network devices, legacy devices and applications, SCADA systems, and other resources such as Microsoft Entra ID (formerly Azure Active Directory).
While LDAP is primarily designed for accessing resources across the network, it necessarily has authentication capabilities built-in to allow secure access to these resources. This means that LDAP can function as an intermediary identity provider (IdP) service between an app and Microsoft Active Directory or other directory services, where user authentication and first factors can be stored.
SurePassID seamlessly adds multi-factor authentication (MFA) to LDAP-federated endpoints by serving as an LDAP IdP. This allows those applications and devices to be incorporated into a "single pane of glass" for complete visibility and audit trail into all user authentications. Meanwhile users benefit from a continuous user experience across all of their logins, including those accomplished via LDAP.
Deployment Options


Cloud
On-Prem


Hybrid Cloud
Air-Gapped
MFA Support


Phishing-Resistant MFA

