One-Time Password (OTP)
Event-based (OATH HOTP)
Time-based (OATH TOTP)
Challenge-Response (OATH OCRA)
Traditional, one-time passcode (OTP) multi-factor authentication (MFA). For use when phishing-resistant MFA is not possible, mandated, or desired.

The one-time password - continuing to deliver cybersecurity value
User access is every organization’s biggest attack surface. Hostile actors exploit it to spread ransomware and penetrate critical infrastructure systems. The result is ever-increasing remediation costs and liability risks.
Enter the one-time password (OTP), a form of traditional multi-factor authentication (MFA). Based on the OATH open reference architecture, it takes the form of three open standard algorithms:
- Event-based OTP (HOTP)
- Time-based OTP (TOTP)
- Challenge-response OTP (OCRA)
While traditional MFA is vulnerable to phishing attacks in which users can be tricked into revealing their access information or other having their access compromised, it continues to deliver cybersecurity value. Traditional MFA is easy to deploy, well-understood by users, cheaper than phishing-resistant MFA, and addresses offline use cases that phishing-resistant MFA cannot.

SurePassID SMS OTP in action
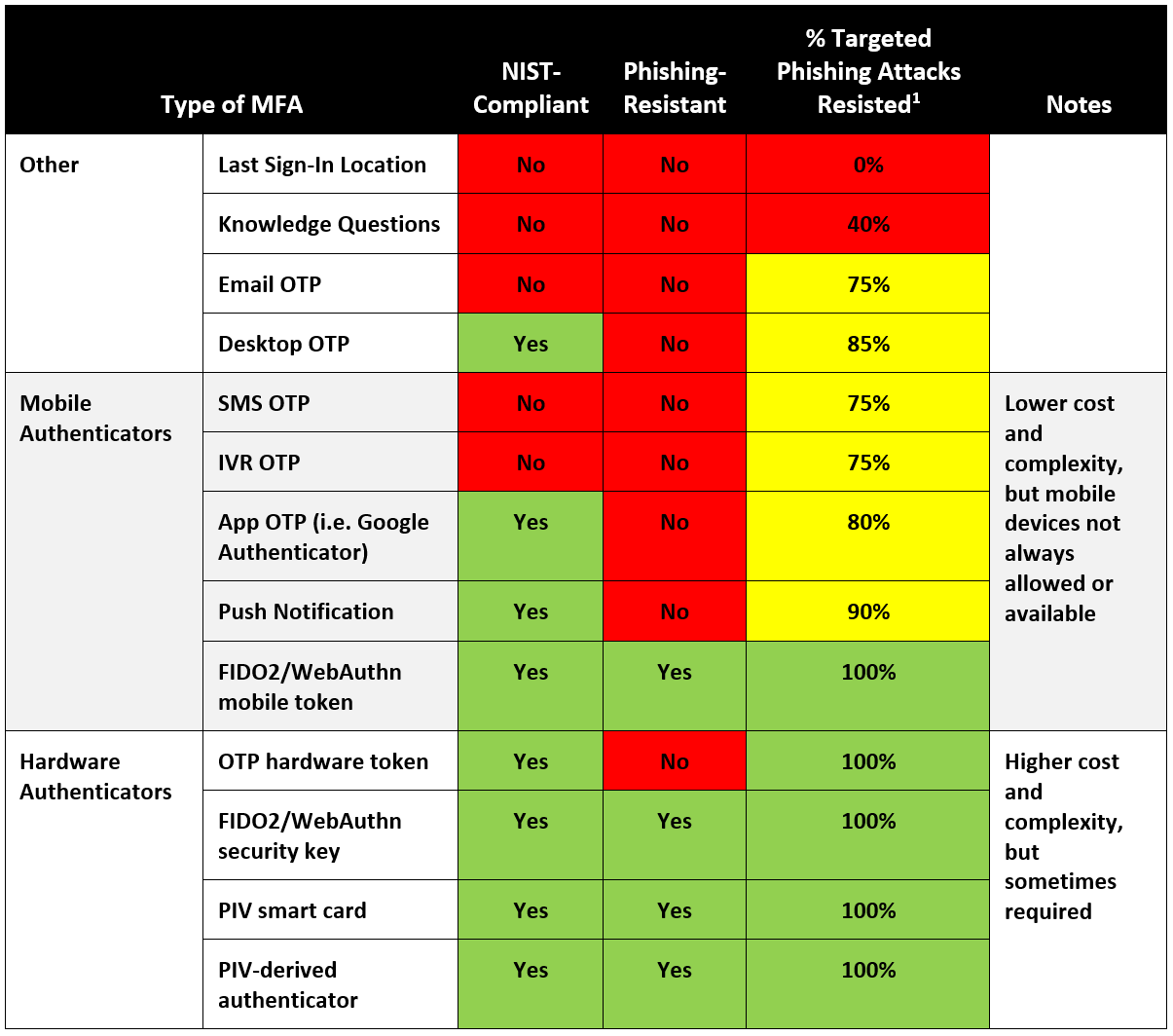
Types of MFA compared
One of the most common questions our MFA experts are asked is, “Is the MFA we’re using compliant – or even or all that secure?”
Not all types of MFA are created equal. Find out why.
What is One-Time Password (OTP) MFA?
An identity and access management security method that requires multiple factors of identification to access resources and data - thus multi-factor authentication (MFA). MFA gives businesses the ability to monitor and help safeguard their most vulnerable information and networks.
Based on OATH
OATH is an open reference architecture for open-standard strong authentication:
- HOTP: An HMAC-based one-time password algorithm (RFC 4226)
- TOTP: Time-based one-time password algorithm (RFC 6238)
- OCRA: OATH Challenge-Response Algorithm (RFC 6287)
Based on secret keys and moving factors
The secret is a static value that is created when you provision a new credential. It is only communicated once, and is stored on both the user's authenticator ("token") and the SurePassID authentication server.
The moving factor changes each time a new OTP is requested. The way the moving factor is generated and validated is different for HOTP and TOTP credentials.
Based on password + OTP (or other second factor)
The first factor in MFA is the user's password, which is typically stored in Microsoft Active Directory (AD) or other identity and management (IAM) system.
The second factor is the OTP generated by the OATH algorithm. However, there are other second factor forms which may be used, typically having to do with user biometrics, device, location, or other "somethings you have."
Vulnerable to phishing attacks
The great shortcoming of traditional MFA is its vulnerable to phishing attacks. Types of these attacks include:
- Spear phishing
- Smishing
- Vishing
- Brute force attacks
- Man-in-the-middle attacks
- Replay attacks
- Credential stuffing
SurePassID fully supports MFA via OATH
Event-based (HOTP)
The OATH HOTP algorithm is an mixes a secret key with a counter factor that is incremented every time the user actives the token.
Time-based (TOTP)
The OATH TOTP algorithm mixes a secret key with a current time interval, which means that the server and token time must match.
Challenge-response (OCRA)
The OATH OCRA algorithm allows using data signing like Confirm What You See (CWYS) to reinforce the OATH security and payments security in particular.
Interactive voice recognition
Interactive voice recognition (IVR) is a critical method of traditional MFA for visually-impaired users who cannot see an OTP code to enter it.
Trying to understand whether OTP is right for you?
SurePassID can help. As experts with MFA in our DNA, we bring decades of experience to bear on your situation and use cases.











