Authentication Methods
Phishing-Resistant MFA
One-Time Password (OTP)
Mobile Push
Short Message Service (SMS)
Interactive Voice Response (IVR)
Backup Methods
SurePassID supports the widest range of open standard authentication methods to address every use case.

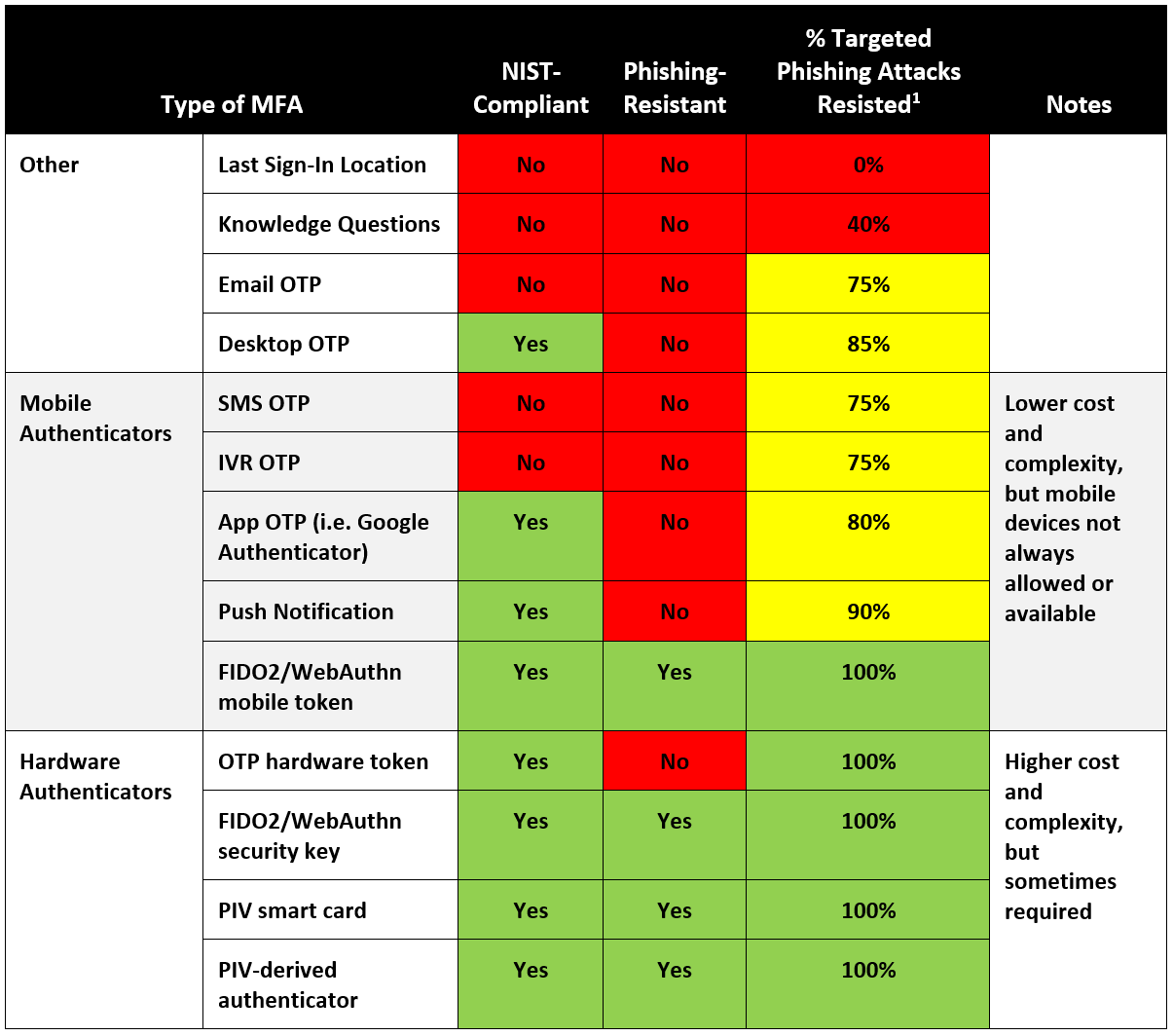
Types of MFA compared
SurePassID supports every open standard multi-factor authentication (MFA) method, ensuring that our customers have maximum flexibility without vendor lock-in.
But what are the different types of MFA? And do they quality as phishing-resistant and NIST-compliant - or even all that secure?
Those are two of the most common questions that our MFA experts answer.
Not all types of MFA are created equal. Each one represents a trade-off between multiple factors:
- Cost
- Security
- Complexity
- End user experience
If you have questions about the right type or types of MFA for your enterprise, SurePassID has the answers and guidance you need.








Phishing-Resistant MFA via FIDO2/WebAuthn
Based on the open standard from W3 (WebAuthn) and FIDO Alliance (FIDO2), FIDO2/WebAuthn is a phishing-resistant, passwordless multi-factor authentication (MFA) method that enables insecure password-only logins to be replaced with secure and fast login experiences across websites and apps.
Phishing-Resistant
NIST Compliant
Resisted 100% of Targeted Phishing Attacks
One-Time Password (OTP) via OATH HOTP/TOTP/OCRA
One time passwords (OTPs) are an authentication method used as part of two-factor authentication (2FA) and multi-factor authentication (MFA):
- Something you know (Username/Password); and
- Something you have (One Time Password)
OTPs are unique passwords that are only valid for a single login session for a defined period of time. OTPs are generated via the open standard OATH HOTP (event-based) or TOTP (time-based) algorithm. A variety of user authenticators can be used to generate OTPs, or they can be generated separately and sent to users via SMS, IVR, email or other means.
NIST Compliant
Resisted 100% of Targeted Phishing Attacks - Hardware OTP
Resisted 80% of Targeted Phishing Attacks – Mobile App OTP
Resisted 75% of Targeted Phishing Attacks – Email OTP
Phishing-Resistant






Mobile Push Authentication
SurePassID Authentication Server turns any mobile device – BYOD or issued – into a universal authenticator for fast, frictionless MFA. With a single tap, users can verify their identity and begin securely accessing resources. Alternatively, users can easily deny unrecognized login attempts and prevent bad actors from unauthorized access. Best of all, push authentication is highly secure as an MFA out-of-band and anti-replay attack method.
NIST Compliant
Resisted 90% of Targeted Phishing Attacks
Phishing-Resistant


Short Message Service (SMS)
Mobile devices with SMS text capability can be used for authentication via One Time Password (OTP) and Challenge/Response (CR or Y/N). This is a less-secure form of strong authentication because it is vulnerable to man-in-the-middle attacks.
- SMS OTP sends an OTP to the user’s phone via SMS. The user enters the OTP into their login authentication and is approved.
- SMS Challenge-Response sends a question asking if the authorization attempt is approved to the user’s phone via SMS. If the user texts back “Yes”, authentication is completed and the user is logged in. If the user texts back “No”, authentication is failed and the user is not logged in.
For organizations requiring compliance with any NIST-based regulatory regime, SMS OTP is no longer a compliant authentication method due to its vulnerability to man-in-the-middle (MITM) attacks.
Phishing-Resistant
NIST Compliant
Resisted 75% of Targeted Phishing Attacks
Interactive Voice Response (IVR)
Mobile phones can be used for authentication via One Time Password (OTP) or Challenge-Response (CR or Y/N) delivered via Interactive Voice Response (IVR). This is a less-secure form of strong authentication because it is vulnerable to man-in-the-middle (MITM) attacks.
- IVR OTP places a voice call to the user, who listens to the OTP. Then the user enters the OTP into their login authentication and is approved.
- IVR Challenge-Response places a voice call to the user, who listens to a question asking if the authorization attempt is approved. If the user replies “Yes”, authentication is completed and the user is logged in. If the user replies “No”, authentication is failed and the user is not logged in.
For organizations with visually-impaired users, IVR Challenge/Response enables compliance with the Americans with Disabilities Act (ADA). However, IVR authentication is not compliant with NIST-based regulatory regimes due to its security vulnerability.
Phishing-Resistant
NIST Compliant
Resisted 75% of Targeted Phishing Attacks


Backup Methods
At SurePassID, we know one size doesn’t fit all when it comes to MFA – and backup authentication methods. Different organizations have different use cases and requirements. Thus we offer the widest variety of backup authentication methods.
SurePassID Authentication Server enables any authentication method to be used as a backup authentication method. Administrators can specify the backup authentication method or methods for any given user account. Alternatively, users can be allowed to choose their own backup method or methods from a pre-approved list.
For additional security, backup authentication methods can be specified for emergencies only. Once used, an alert can be sent to IT security or helpdesk staff for human intervention, or the user account can operate on a less-privileged basis according to security policies.
Contact sales
We look forward to providing the authentication solution and pricing you need
+1 (888) 200-8144
SurePassID, Corp.
360 Central Avenue
First Central Tower
Suite 800
St. Petersburg FL 33701
MFA questions? Talk to an expert
Need support? Visit support.surepassid.com
