Compliance
Not only is MFA a powerful solution to maintain compliance with industry regulations, but it's also now a prerequisite for qualifying for cyber insurance.
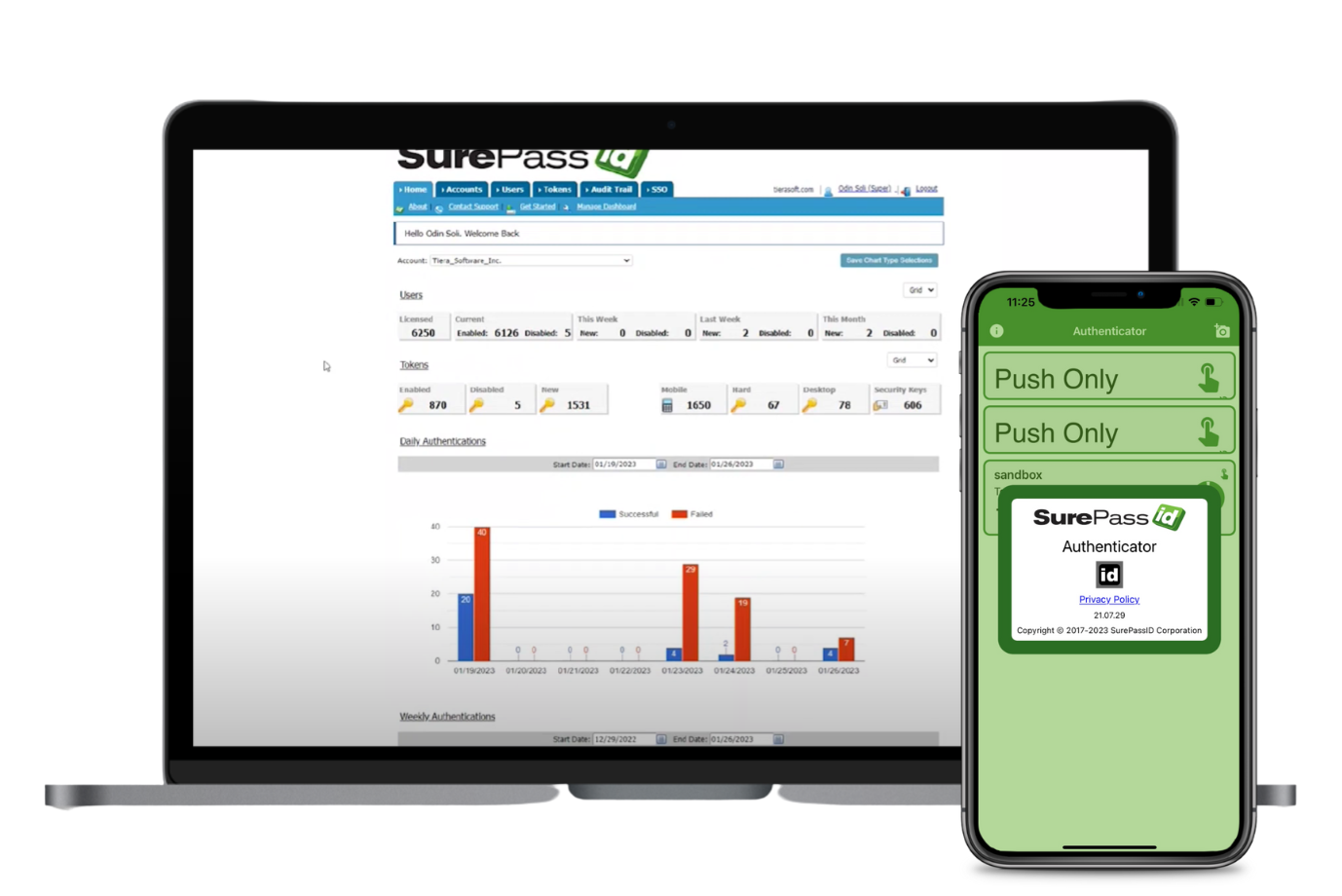
Regulatory Compliance Standards
Regulations that typically require the implementation of multi-factor authentication include:
-
The General Data Protection Regulation (GDPR): GDPR is a regulation enacted by the European Union to protect the data privacy of European citizens. The regulation requires businesses in the EU or those that process personal data of EU residents to implement measures to secure their data. MFA is one of the recommended measures.
-
National Institute of Standards and Technology (NIST) guidelines: NIST guidelines recommend that login access to sensitive areas must require more than just a password. MFA is a requirement for many business practices, including IT systems access, email access, and remote access protocols.
-
Payment Card Industry Data Security Standard (PCI DSS): PCI DSS is a regulatory standard that payment cardholders and merchants must follow. The standard mandates security features that businesses must implement to ensure payment information security. MFA is one of the recommended security features.




Steps to Ensure Compliance
To ensure compliance with regulatory standards, businesses must take the following steps:
Determine Which Regulations Apply
Identify which regulatory compliance standards apply to your business. This can be achieved through working with a compliance consultant or legal professional.
Develop an MFA Policy
Develop an MFA policy with the requirements appropriate for your business.
Train Employees
Train employees on MFA policies and procedures. This can be in the form of virtual training sessions, workshops or training webinars to ensure that everyone within the company has the required knowledge and is following the policies in place.
Test the MFA System
Periodically test the MFA system to ensure that it adheres to your business's MFA policies.
Address Any Non-Compliance
If your business is not compliant, take action to address any issues immediately. Depending on the severity of the violation, this may include making updates to policies and procedures or discontinuing use of certain systems.
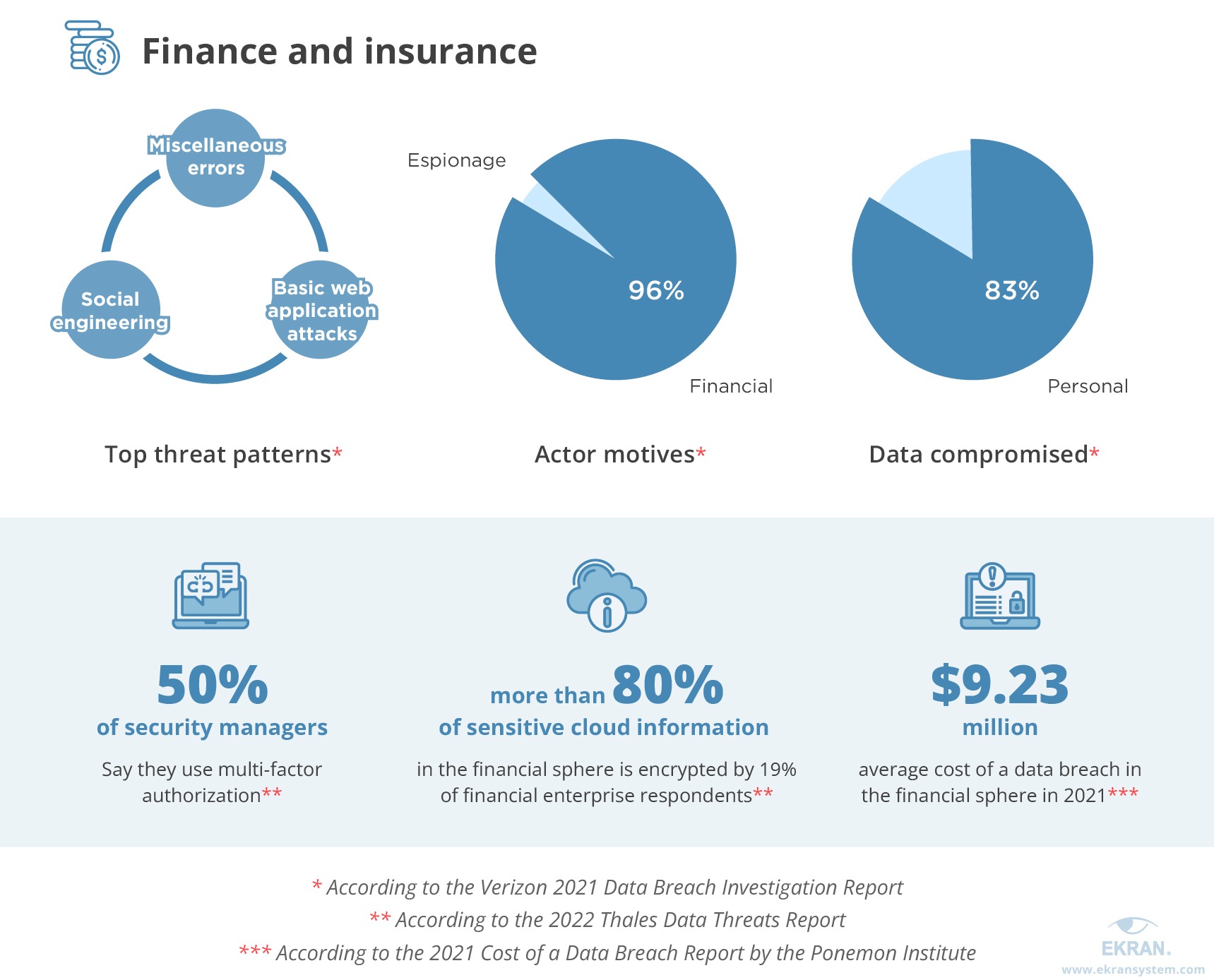
Zero Trust
As regulatory compliance standards continue to evolve, MFA will need to adapt to comply with them. One current trend is the push towards Zero Trust Architecture, which assumes that every user and device on a network is a potential threat, requiring MFA for every access attempt.
SurePassID's adaptive and continuous authentication policies make it easy to verify user identities across all environments, whether you're using SurePassID or any third-party MFA. By constantly monitoring the network's critical assets, users, services, and data, you have the power to prioritize and create customized security policies that truly protect your organization. With SurePassID, you can rest easy knowing that your user identities are continuously verified and your data is always secure.

SurePassID Universal Server works with all open-standard authenticators
Authenticators are the user experience of MFA. SurePassID works with all open-standard authenticators, enabling you to meet any use case or budget requirement.
With SurePassID you can mix-and-match authenticators for specific users or user categories, and import any existing tokens you may have.
Frequently asked questions about SurePassID
What are SurePassID's deployment modes?
- Software-as-a-Service (SaaS Public, SaaS Private)
- Windows Installer Package (Microsoft Windows Server 2012-2022, any edition, and Microsoft Windows 8-11)
- Virtual Machine (Microsoft Hyper-V)
- Container Image (Docker/Kubernetes, Microsoft ACI, Amazon ECS)
- Embedded (Windows 7 or later, Linux OpenEmbedded for 32/64-bit ARM/PPC/MIPS/x86)
- Secure Element (NXP EdgeLock SE050/SE051, NXP A71CH/A71CL/A1006)
How long does it take to deploy SurePassID?
Cloud deployments can occur same day.
On-premise and air-gapped deployments will vary depending on the complexity of your requirements.
Regardless, our Customer Success team will be with you every step of the way.
Can SurePassID integrate with my IAM solution?
As a SAML 2.0 IdP, SurePassID easily and seamlessly adds MFA to any existing IAM solution, such as Okta or Ping Identity.
SurePassID also integrates with Third-Party directory services, such as Workday, Oracle, and SAP.
We even integrate with legacy SCADA systems that have built-in user directories.
What makes SurePassID better than other MFA solutions?
- Unmatched on-premise and air-gapped capabilities
- Outstanding technical support
- Unbeatable value
How secure is SurePassID?
SurePassID is the most hardened MFA solution on the market. We never stop innovating to protect our customers from evolving cyberthreats.
- USA company
- Secure SBOM (Software Bill of Materials)
- Secure user and token provisioning (QR code to one-time-use provisioning page)
- Comprehensive logging and audit trail
- FIPS 140 mode
- AES 256 encryption for data at rest
- SHA 256 or SHA 512 encryption for data in iransit
- And much more...
How much does SurePassID cost?
Visit https://www.surepassid.com/pricing for a complete guide to SurePassID Authentication Server pricing and features.
An MFA solution should be a game changer
See how SurePassID can help you authenticate anywhere, eliminate passwords, and use one solution.