Access Control
Windows, MacOS, Unix/Linux domain and account logins
VPNs and RDP/SSH remote access
Legacy apps and devices
SurePassID's advanced, deploy-anywhere MFA platform easily and cost-effectively adds multi-factor authentication (MFA) to your access control points.

MFA with offline 2FA for Windows Logon Manager
SurePassID keeps Windows domain and account logons secure – in all use cases. SurePassID seamlessly integrates with Microsoft Windows client and server operating systems to add multi-factor authentication (MFA) to local and Remote Desktop logins. Enforcing Zero Trust and maintaining secure access to company resources has never been easier.
But what if the user is offline when trying to login? Then SurePassID automatically falls back to a compliant HMAC-based one-time password (OATH HOTP) authentication method and an OTP generated by their Push Authenticator app or other registered authenticator. The result is seamless end-to-end authentication with no inconvenience to the user or calls to your helpdesk.
.webp)


MFA for MacOS/Unix/Linux with PAM
SurePassID seamlessly adds MFA to MacOS and Linux domain and account logons via the privileged access module (PAM) functionality. No longer do machines running flavors of Unix need to be ignored or special-cased when it comes to MFA. Users simply log into them using the same SurePassID solution and authenticators ("tokens") that they use to log into any other system.
SurePassID has PAMs for MacOS and all major distros of Linux, including:
- RHEL (Red Hat Enterprise Linux)
- SUSE
- Centos
- Ubuntu
MFA for Virtual Private Networks (VPNs)
SurePassID quickly and easily adds MFA to VPN software and hardware solutions that are used for remote access. From newest VPNs to legacy VPNs, we have a solution for you.
For modern VPNs that support the FIDO2/WebAuthn protocol, SurePassID enables you to use passwordless, phishing-resistant MFA, as well as Push, OTP, and Challenge-Response authentication methods.
For legacy VPNs that do not support the FIDO2/WebAuthn protocol, SurePassID enables you to use Push, OTP, and Challenge-Response authentication methods.
Supported VPN hardware vendors include Cisco, Zyxel, GL.iNet, Netgear, UTT, Dell Sonicwall, D-Link, and Linksys.

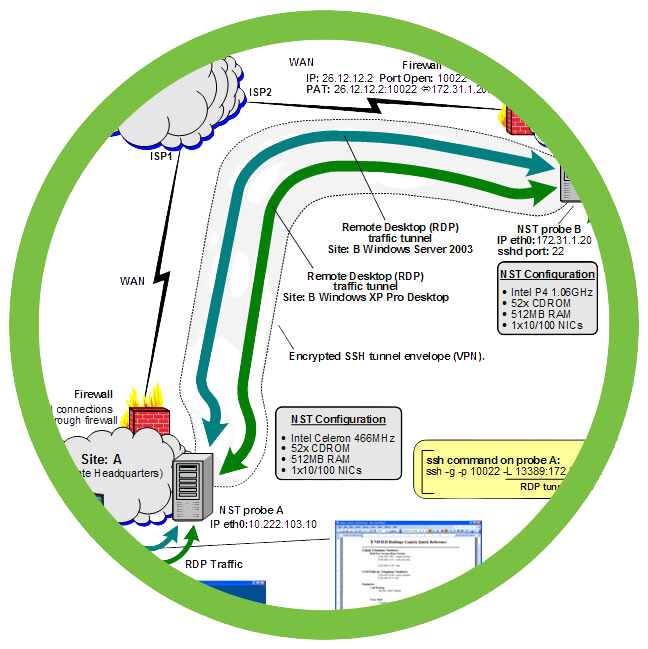
MFA for RDP and SSH
Connecting remotely to workstations and server infrastructure is an everyday occurrence for IT/OT organizations – and a focus of ransomware gangs and hostile state actors exploiting security breaches. No matter whether you’re using Windows Remote Desktop Protocol (RDP) or Secure Shell (SSH) protocol, securing remote access on local consoles or via incoming connections is essential to Zero Trust and regulatory compliance.
SurePassID Authentication Server seamlessly integrates with your identity provider and RDP or SSH servers to secure remote access with MFA. For RDP, Credentialed User Access Control (UAC) elevation requests can invoke MFA depending on your Windows UAC configuration. For SSH, MFA can be applied to both Shells and Tunnels. The result is RDP/SSH multi-factor authentication that you can rely upon.
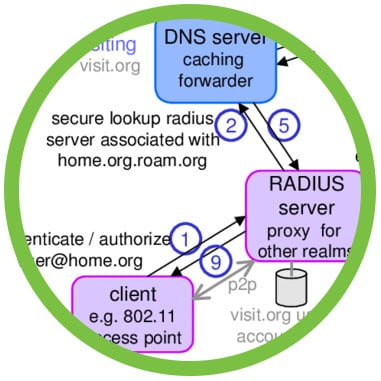
MFA for RADIUS and TACACS+ via Cisco ISE
SurePassID Authentication Serve can secure any RADIUS-compliant or TACACS+ system such as Microsoft Universal Access Gateway, VPN routers/devices, Citrix applications, Wi-Fi access points, FreeRADIUS on Linux distros, Cisco applications, and more. SurePassID supports key features such as:
- Challenge Response – The server “challenges” the user for any of their registered assigned credentials. Most challenges will be to provide a One Time Password (OTP) after successfully entering a valid username and password. (Some RADIUS and TACACS+ devices only support single-factor authentication, in which case two-factor authentication (2FA) is added by appending the OTP to the user’s password.)
- Proxy Server Chaining – In RADIUS authentication, there are often multiple RADIUS servers as part of the authentication process.
- nFactor Authentication Framework – Enables organizations to define dynamic authentication methods at the time of authentication on a user by user basis.
But SurePassID’s strengths don’t end there. As a highly extensible solution, our platform encompasses on-prem, cloud, and hybrid deployment architectures. No matter what your RADIUS or TACACS+ clients and remote access gateways look like, SurePassID can secure it with RADIUS and TACACS+ multi-factor authentication.

Reverse Proxy MFA
Adding MFA to legacy devices and shop floor equipment isn't always easy. They often lack modern interface points, are not connected to Active Directory (AD), do not support modern authentication methods, and may not even support the concept of user accounts.
In those challenging IT/OT situations, SurePassID deploys a reverse proxy MFA solution using NGINX. That enforces MFA and creates an audit trail by requiring users to log into the reverse proxy before they can access the legacy devices or equipment.